
AES encryption in conzept 16
In addition to the previously announced signature functions (see Signieren mit CONZEPT 16), the procedures will be expanded to include encryption and decryption commands, which
Contact: | +49 6104 660-0
vectorsoft.de » Blog » Programming » Page 4

In addition to the previously announced signature functions (see Signieren mit CONZEPT 16), the procedures will be expanded to include encryption and decryption commands, which
For interoperability with other development tools (or applications created with them), conzept 16 provides a general interface: the external programming interface. Like the other components,
Sorting character strings alphabetically is an effective way of quickly finding the element you are looking for in a list. The sorting of character strings

We have already written several articles on the new features for version 5.7.08, which is scheduled for the end of August. However, in addition to

The GroupTile object allows the user to customize the size of display areas. The object can also contain a title bar, which can be used

Digital signatures are used in many areas where authenticity and integrity play an important role. Examples include e-mails, invoices and electronic ID cards. As a

To process procedures, the executable procedure code must be in the main memory. conzept 16 only loads the code from the database that is actually
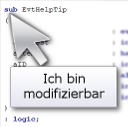
Many suggestions for conzept 16 relate to the modification of help tips before they are displayed or to a reaction to sub-objects. In order to
With CtxDocEdit, conzept 16 provides developers with an object that can be used to implement professional word processing. In addition to functions such as processing
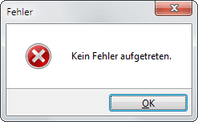
No application can do without message windows (also known as message boxes or dialog boxes). Be it to inform the user, ask for confirmation or

With the RecView and the RecList, conzept 16 provides two objects with which data records of a table can be displayed very easily. Depending on

Encrypted connections are indispensable today when non-public data is to be transported via the Internet. In view of the activities of secret services and criminals,
Vectorsoft AG (‘Provider’) provides a public blog for Internet users (‘Users’) on the vectorsoft.de website. The public blog is intended for the exchange of information and ideas. Users who participate with contributions and comments undertake to comply with the blog terms of use and are responsible for the accuracy, appropriateness and freedom from legal infringements of their contributions. By using the comment function in our blog, you accept these terms of use.
We ask you to refrain from personal attacks and provocations based on other opinions. Please argue objectively and maintain a constructive discussion culture. Your comment should always be related to the topic in question in order to avoid digressions into other topics. Posting the same comment or several similar comments more than once is not permitted.
By submitting your comment, you confirm that you are not violating any copyrights or other rights of third parties. Inciting, racist statements, instructions for criminal offences and their glorification, depictions of violence, pornographic content and statements that violate personal rights are prohibited.
The use of the comment function is not permitted for commercial or party-political purposes. Advertising contributions of any kind will be deleted immediately.
When entering your name, pay attention to the principles mentioned above.
If you intend to publish quotes or contributions from third parties, please indicate the respective sources and explain how they relate to the blog post.
Posts that violate this policy will be deleted immediately. If you notice any violations yourself, please send us the link to the comment in question by e-mail to . We expressly point out that we will exclude individual users in the event of repeated or serious violations of these terms of use.
As of: Sept. 2024