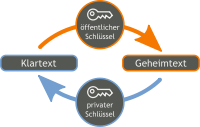
For some time now, it has been possible to encrypt data via AES (symmetrisch) with conzept 16. The shared secret key must first be exchanged between the communication partners in a different way. With the upcoming version of conzept 16, the MemEncrypt() commands will be expanded to include options for encrypting and decrypting data with RSA.
New options
The following options are added:
_MemCipherRSA– Use RSA as the encryption method_MemKeyAsymPrivate/_MemKeyAsymPublic– Selection of the type of key specifieds_MemPaddingRSAPkcs1/_MemPaddingRSAOaep– Selection of the padding that is supposed to be used
Key
As before, the private or public key used can be specified as a hexadecimal or Base64-encoded character string or as a memory object. If the key is specified as a character string, it must not be longer than 4096 characters in decoded form.
Padding
Beim Ver- und Entschlüsseln muss jeweils das gleiche Padding verwendet werden. Mit dem Padding wird der Block auf die Schlüssellänge aufgefüllt. In vielen bestehenden Projekten (außerhalb von conzept 16) wird bisher das PKCS #1 () verwendet. Dieses benötigt mindestens 11 Zeichen. Für neuere Projekte ist jedoch das OAEP-Padding () zu empfehlen. Hierfür werden am Ende des Blockes mindestens 42 Zeichen benötigt. Das OAEP-Padding kann beim Verschlüsseln jedoch nur mit dem öffentlichen Schlüssel und beim Entschlüsseln nur mit dem privaten Schlüssel (_MemKeyAsymPrivate) angegeben werden.
The same padding must be used for both encryption and decryption. The padding is used to fill the block to the key length. In many existing projects (outside of conzept 16), PKCS #1 (_MemPaddingRSAPkcs1) has been used up to now. This requires at least 11 characters. For newer projects, however, OAEP padding (_MemPaddingRSAOaep) is recommended. This requires at least 42 characters at the end of the block. However, OAEP padding can only be specified with the public key _MemKeyAsymPublic when encrypting and only with the private key (_MemKeyAsymPrivate) when decrypting.
Key generation
As RSA, unlike AES, does not simply use a random character string as a key, but a key pair must be generated, there is also the MemGenKeyPair(aMemKeyPrivate, aMemKeyPublic, aKeyLenBit) command. This generates a private and the corresponding public RSA key in the specified bit length and fills the specified memory objects. With regard to the key length, it should be noted that the encryption and decryption for longer keys also takes longer. Nevertheless, key lengths of less than 2048 bits are no longer recommended nowadays.
Application
Asymmetric encryption is only possible for comparatively small data. The length of the encryptable data, minus the padding, is identical to the key length. For example, with a key length of 2048 bits = 256 characters. If more data is supposed to be encrypted, hybrid encryption is recommended. This involves generating a random key for AES, which is encrypted with RSA. The user data is then encrypted with the random AES key.
sub Encrypt
(
aMemData : handle;
)
: int;
local
{
tMemKey : handle;
tRes : int;
}
{
// Create memory object for public key and load key
tMemKey # MemAllocate(_MemAutoSize);
tMemKey->LoadPublicKey();
// Encrypt data, release memory object and return result
tRes # aMemData->MemEncrypt(_MemCipherRSA | _MemKeyMem | _MemKeyAsymPublic | _MemPaddingRSAOaep, NULL, NULL, 1, _MemDataLen, NULL, 1, tMemKey);
tMemKey->MemFree();
return tRes;
}An example of encrypted communication will be included in the CodeLibrary.